Systems and Means of Informatics
2021, Volume 31, Issue 4, pp 48-60
ON ONE METHOD FOR DETECTING EXPLOITATION OF VULNERABILITIES AND ITS PARAMETERS
Abstract
When a program vulnerability is successfully exploited, the exploit often calls some system function. Therefore, one of the possible ways to detect exploitation of a vulnerability of a specific program is to check for atypical distance between the call with
the number i and the call with the number i - j where j 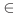 {1,..., T}, T {1,..., T}, T 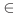 N. Distance is understood as the difference
between the addresses of the call of these functions and the typicality is determined by checking whether it belongs to the distance profile. In addition to the T parameter, the detection algorithm
uses the parameter W( N. Distance is understood as the difference
between the addresses of the call of these functions and the typicality is determined by checking whether it belongs to the distance profile. In addition to the T parameter, the detection algorithm
uses the parameter W(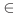 N): it is the number of profiles against which the call is checked. In this case, for j N): it is the number of profiles against which the call is checked. In this case, for j 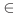 {1, . . . , W}, the profile with the number j is constructed from pairs of calls from a legitimate sequence, the difference of call indices in which is equal to j. The aim of this work is, on the one hand, to describe the detection algorithm and, on the other, to provide an experimental estimate of the sufficient values of the parameters W and T. As a result, in particular, it was found that the values of these parameters depend on the set of monitored functions; therefore, for each set of functions (and each protected program), these parameters must be found separately. {1, . . . , W}, the profile with the number j is constructed from pairs of calls from a legitimate sequence, the difference of call indices in which is equal to j. The aim of this work is, on the one hand, to describe the detection algorithm and, on the other, to provide an experimental estimate of the sufficient values of the parameters W and T. As a result, in particular, it was found that the values of these parameters depend on the set of monitored functions; therefore, for each set of functions (and each protected program), these parameters must be found separately.
[+] References (8)
- Rohlf, C., and Y. Ivnitskiy. 2011. Attacking clientside JIT compilers. Black Hat USA. Available at: https://www.nccgroup.trust/globalassets/resources/us/ presentations/documents/attacking_cl ientside_jit_compilers.pdf (accessed September 22, 2021).
- Forrest, S., S. Hofmeyr, and A. Somayaji. 2008. The evolution of system-call monitoring. Annual Computer Security Applications Conference Proceedings. Piscataway, NJ: IEEE. 418-430. doi: 10.1109/ACSAC.2008.54.
- Singh, A., R. Arora, and H. Pareek. 2017. Malware analysis using multiple API sequence mining CFG. arXiv.org. 12 p. Available at: https://arxiv.org/abs/1707.02691 (accessed September 18, 2021).
- Gupta, S., H. Sharma, and S. Kaur. 2018. Malware characterization using Windows API call sequences. J. Cyber Security Mobility 7(4):363-378. doi: 10.1007/978-3- 319-49445-6_15.
- Snow, K. Z., F. Monrose, L. Davi, A. Dmitrienko, C. Liebchen, and A.-R. Sadeghi. 2013. Just-in-time code reuse: On the effectiveness of fine-grained address space layout randomization. Symposium on Security and Privacy Proceedings. Piscataway, NJ: IEEE.
574-588. doi: 10.1109/SP.2013.45.
- Wagner, D., and P. Soto. 2002. Mimicry attacks on host-based intrusion detection systems. 9th Conference on Computer and Communications Security Proceedings. New York, NY: ACM. 255-264. doi: 10.1145/586110.586145.
- Nurmuhametov, A. R., E. A. Zhabotinskij, Sh. F. Kurmangaleev, S. S. Gajsarjan, and A.V. Vishnjakov. 2017. Melkogranulyarnaya randomizatsiya adresnogo prostranst- va programmy pri zapuske [Fine-grained address space layout randomization on program load]. Trudy ISP RAN [ISP RAS Proceedings] 29(6):163-182. doi: 10.15514/ ISPRAS-2017-29(6)-9.
- Kosolapov, Y. V. 2020. On detecting code reuse attacks. Autom. Control Comp. S. 54:573-583. doi: 10.3103/S0146411620070111.
[+] About this article
Title
ON ONE METHOD FOR DETECTING EXPLOITATION OF VULNERABILITIES AND ITS PARAMETERS
Journal
Systems and Means of Informatics
Volume 31, Issue 4, pp 48-60
Cover Date
2021-12-10
DOI
10.14357/08696527210405
Print ISSN
0869-6527
Publisher
Institute of Informatics Problems, Russian Academy of Sciences
Additional Links
Key words
software vulnerabilities; distance between function calls; program protection
Authors
Yu. V. Kosolapov 
Author Affiliations
 Institute for Mathematics, Mechanics, and Computer Science named after I.I. Vorovich, Southern Federal University, 8a Milchakova Str., Rostov-on-Don 344090, Russian Federation
|
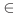 {1,..., T}, T
{1,..., T}, T 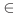 N. Distance is understood as the difference
between the addresses of the call of these functions and the typicality is determined by checking whether it belongs to the distance profile. In addition to the T parameter, the detection algorithm
uses the parameter W(
N. Distance is understood as the difference
between the addresses of the call of these functions and the typicality is determined by checking whether it belongs to the distance profile. In addition to the T parameter, the detection algorithm
uses the parameter W(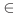 N): it is the number of profiles against which the call is checked. In this case, for j
N): it is the number of profiles against which the call is checked. In this case, for j 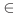 {1, . . . , W}, the profile with the number j is constructed from pairs of calls from a legitimate sequence, the difference of call indices in which is equal to j. The aim of this work is, on the one hand, to describe the detection algorithm and, on the other, to provide an experimental estimate of the sufficient values of the parameters W and T. As a result, in particular, it was found that the values of these parameters depend on the set of monitored functions; therefore, for each set of functions (and each protected program), these parameters must be found separately.
{1, . . . , W}, the profile with the number j is constructed from pairs of calls from a legitimate sequence, the difference of call indices in which is equal to j. The aim of this work is, on the one hand, to describe the detection algorithm and, on the other, to provide an experimental estimate of the sufficient values of the parameters W and T. As a result, in particular, it was found that the values of these parameters depend on the set of monitored functions; therefore, for each set of functions (and each protected program), these parameters must be found separately.